What to Do If You’re on “Have I Been Pwned”: Actionable Steps After a Data Breach
Discovering that your personal information has been compromised in a data breach can be alarming. Websites like “Have I Been Pwned” provide a valuable service by informing you if your data appears in known breaches. If you find your information on such a site, here’s a comprehensive guide on how to respond effectively.
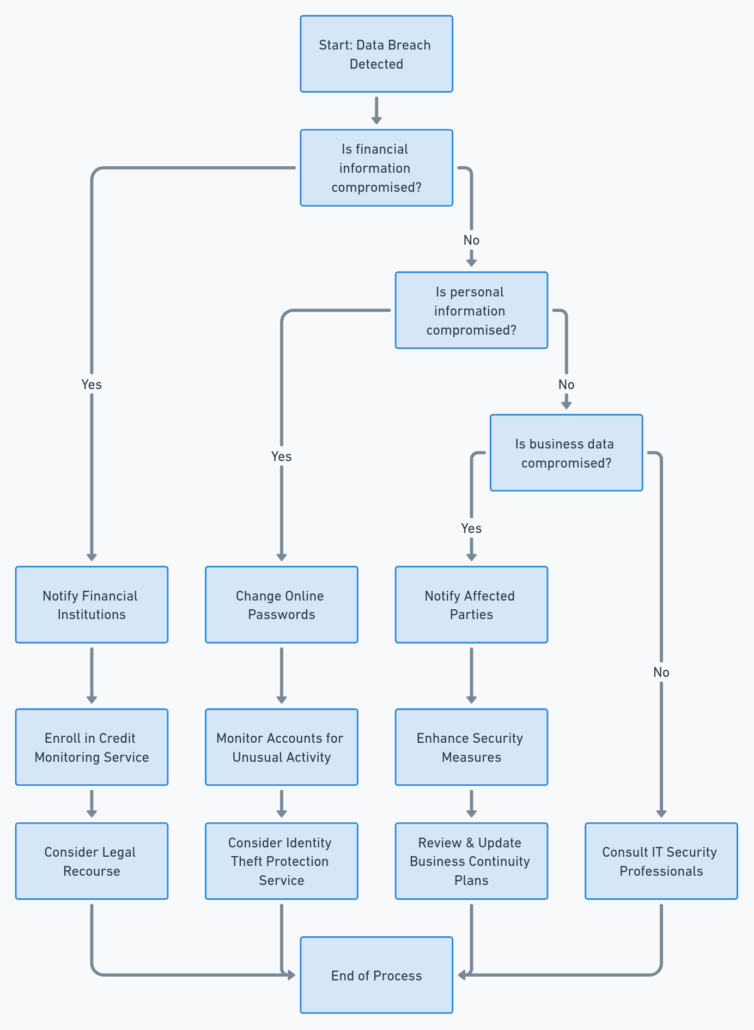
Step 1: Change Your Passwords Immediately If your email is listed on “Have I Been Pwned,” start by changing the password for the affected account. Don’t stop there; change passwords for other accounts where you’ve used the same or similar credentials. Use strong, unique passwords for each account, and consider using a password manager to keep track of them.
Step 2: Enable Two-Factor Authentication (2FA) Add an extra layer of security to your accounts by enabling two-factor authentication. This requires a second form of verification, such as a text message or an authentication app, to access your account, even if someone has your password.
Step 3: Monitor Your Accounts for Suspicious Activity Keep a close eye on your accounts for any unusual activity. This includes your financial accounts, email, and social media. If you notice anything odd, report it immediately and take appropriate actions to secure your account.
Step 4: Be Alert to Phishing Attempts After a breach, scammers might target you with phishing emails or messages, pretending to be legitimate companies or services. Be skeptical of any communications asking for personal information or urging you to click on links.
Step 5: Consider a Credit Freeze or Fraud Alert If sensitive financial information was compromised, consider placing a credit freeze or fraud alert on your credit reports. This can prevent identity thieves from opening new accounts in your name.
Step 6: Stay Informed About the Breach Try to learn as much as you can about the breach. Understanding what information was stolen and how it’s being potentially misused can help you take more targeted actions to protect yourself.
Step 7: Use Credit Monitoring Services If the breach involves your financial data, sign up for credit monitoring services. Many companies involved in a breach offer free monitoring for a certain period. These services alert you to changes in your credit report, helping you respond to unauthorized activities promptly.
Step 8: Update Your Security Questions If your security questions could be answered with information exposed in the breach, change them. Choose questions and answers that are not easily guessable.
Step 9: Educate Yourself on Data Security Use this experience as a prompt to educate yourself on data security best practices. Understand how to protect your information online and be proactive in your cybersecurity measures.
Step 10: Legal Recourse In some cases, you might have legal recourse, especially if the breached entity failed to protect your data adequately. It can be beneficial to consult with a legal professional to explore your options.
Conclusion: Finding your information on “Have I Been Pwned” is a clear sign to take immediate action to secure your digital life. By following these steps, you can mitigate the potential damage from the breach and strengthen your defenses against future incidents. Remember, in the digital world, vigilance is your best ally in protecting your personal information.



Leave a Reply
Want to join the discussion?Feel free to contribute!