Mastering Azure DevSecOps: A Complete Implementation Guide
Introduction
Modern software development demands rapid release cycles while maintaining strong security and compliance.
Azure DevOps offers a powerful suite of tools to streamline development, testing, and deployment.
When combined with Azure DevSecOps principles—shifting security “left” into the earliest stages of development—you create an environment where innovation thrives without compromising on security or governance.
Why Implement Azure DevSecOps?
- Enhanced Security Posture
- Cost of Not Doing So: Vulnerabilities discovered late in the cycle lead to expensive patching, reputational damage, and potential regulatory fines.
- Result: Early security checks reduce incidents, ensuring safer releases and better public trust.
- Efficient Delivery & Collaboration
- Cost of Not Doing So: Siloed teams, manual checks, and repeated rework bog down development.
- Result: Collaborative pipelines align developers, security engineers, and ops teams for faster, more reliable deployments.
- Scalability and Flexibility
- Cost of Not Doing So: Inability to handle surges in workload or new feature demands can cripple your product’s competitiveness.
- Result: Automated CI/CD and standardized security measures let you scale confidently across teams, apps, and geographies.
- Compliance & Governance
- Cost of Not Doing So: Non-compliance with industry standards (e.g., PCI DSS, HIPAA, GDPR) can incur hefty fines and legal ramifications.
- Result: Policy-driven pipelines and integrated audit trails simplify compliance reporting and reduce risk.
Project Setup
A well-structured project lays the groundwork for successful DevSecOps. Clear governance, well-defined repository strategies, and stakeholder alignment ensure everyone moves forward efficiently.
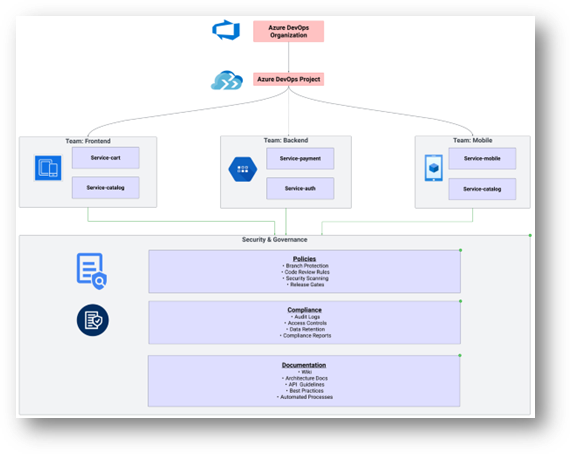
Real-World Example: Project Setup
Scenario:
AcmeRetail, an e-commerce company, has multiple development teams working on overlapping features with little coordination. Repositories are named inconsistently, some are in GitHub, others in on-premises Git, and the rest in Azure Repos. Stakeholders complain about lack of visibility into the development process, confusion around naming conventions, and frequent code conflicts.
Solution:
They decide to unify everything in Azure DevOps. By organizing teams into logical groupings (frontend, backend, mobile), and applying consistent naming conventions (e.g., service-payment, service-cart), they reduce confusion and ensure everyone understands where code lives. They adopt trunk-based development for smaller services and GitFlow for more complex ones.
Best Practices:
- Define clear naming rules for repositories and branches.
- Assign roles such as DevOps Lead, Security Champion, and Product Owner to streamline responsibilities.
- Maintain a single source of truth in Azure DevOps, with consistent policies applied globally.
Action Steps:
- Identify Repositories: Consolidate or migrate all code to Azure DevOps.
- Agree on Branching Strategy: Decide trunk-based vs. GitFlow for each service.
- Set Team Permissions: Limit production pipeline changes to DevOps Leads.
- Document Standards: Publish an internal wiki explaining naming policies, branch strategies, and role definitions.
Setting Up Your Azure DevOps Project
- Define the scope of your Azure DevOps project (teams, repositories, pipelines).
- List key stakeholders and assign roles within Azure DevOps.
- Decide on naming conventions and policies for repositories.
- Define branching strategies (e.g., GitFlow, trunk-based development).
- Specify tools or extensions to integrate with Azure DevOps (e.g., Jira, Slack).
Planning Your DevOps Project
- What are your primary goals for setting up Azure DevOps?
- How will you ensure consistent team onboarding to Azure DevOps?
- Do you need external integrations (e.g., Jira, Slack)? Why?
- What is your plan for scaling DevOps practices as the project grows?
- How will you track and manage technical debt in repositories?
CI/CD Configuration
A robust Continuous Integration and Continuous Deployment (CI/CD) pipeline automates building, testing, and releasing code. By adding security scans and quality gates early, you’ll catch issues before they escalate.
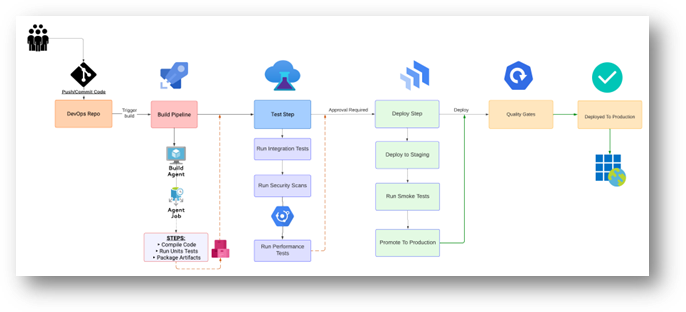
Real-World Example: CI/CD
Scenario
BetaInsurance has a homegrown CI system with manual deployment scripts. Builds often fail due to missing dependencies, and production releases require a senior engineer to run a complex script. The biggest complaint? Slow, unpredictable deployments, and code merges that break previously stable features.
Solution:
They adopt Azure DevOps Pipelines for a standardized YAML-based approach. Each service has a pipeline file that runs on every push to the main branch, automatically building, testing, and scanning the application. Deployment to staging is triggered automatically if all tests pass, and a final manual approval gate pushes changes to production.
Best Practices:
- Keep pipeline definitions in code for transparency and versioning.
- Implement quality gates—like code coverage minimums or linting checks—before merging.
- Use separate build and deployment stages with environment-specific variables.
Action Steps:
- Automate Everything: Write a YAML file containing build, test, and deploy steps.
- Add Approvals: Use manual approval gates for production to prevent accidental deployments.
- Integrate with QA Tools: Automate unit, integration, and performance tests in the pipeline.
- Version Your Builds: Tag each build with semantic versioning to facilitate rollbacks if needed.
Configuring CI/CD Pipelines
- Identify the types of builds required (e.g., debug, production).
- Write the YAML script for a sample pipeline (build/test/deploy).
- Choose environments for deployment (e.g., staging, production).
- Define trigger points for builds (e.g., push to the main branch).
- Add quality gates (e.g., code coverage thresholds, unit test results).
Enhancing CI/CD Workflows
- Are your CI/CD pipelines optimized for scalability?
- What are your dependencies for building and deploying?
- How will you handle rollback scenarios in case of deployment failures?
- Do you have automated tests integrated into your pipelines?
- How will you validate pipeline security during deployments?
Security Integration
Security must become a shared responsibility. Embedding security checks, code scans, and compliance checks within your DevOps process ensures vulnerabilities are caught before code hits production.
Real-World Example: Security Integration
Scenario (Problem):
GammaBank discovered a major SQL injection vulnerability in production just days after a new feature launch. The root cause was a lack of secure coding practices and no static code analysis. Patching took over a week, causing downtime and a hit to customer trust.
Solution:
They integrated SAST (Static Application Security Testing) into the build pipeline, enabling the pipeline to fail if high-severity issues are detected. They also schedule DAST (Dynamic Application Security Testing) runs on their staging environment. Now, security is addressed at every step—before code merges and again before production releases.
Best Practices:
- Treat security as code: define scanning policies in version control.
- Use Azure DevOps extensions or third-party tools for SAST/DAST.
- Involve the security team in daily stand-ups and backlog refinement.
Action Steps:
- Select SAST/DAST Tools: Evaluate marketplace integrations (e.g., WhiteSource, Veracode, OWASP ZAP).
- Define Security Gates: Fail the build if vulnerabilities exceed a defined threshold.
- Adopt a Policy-as-Code Approach: Use Azure Policy or open-source solutions to enforce best-practice configurations.
- Conduct Regular Security Training: Equip developers with secure coding guidelines and threat modeling techniques.
Integrating Security into DevOps
- Select SAST and DAST tools for code and runtime scanning.
- Define security checkpoints in the pipeline (e.g., post-build, pre-deploy).
- List compliance standards relevant to your project (e.g., PCI DSS, HIPAA).
- Create a checklist for validating Infrastructure as Code (IaC) scripts.
- Develop an incident response plan for pipeline vulnerabilities.
Implementing DevSecOps Best Practices
- Are all team members aware of DevSecOps principles?
- How will you ensure compliance across multi-cloud environments?
- What steps are in place to respond to detected vulnerabilities?
- Have you tested your pipeline for false-positive alerts?
- Are you using policy-as-code to enforce best practices?
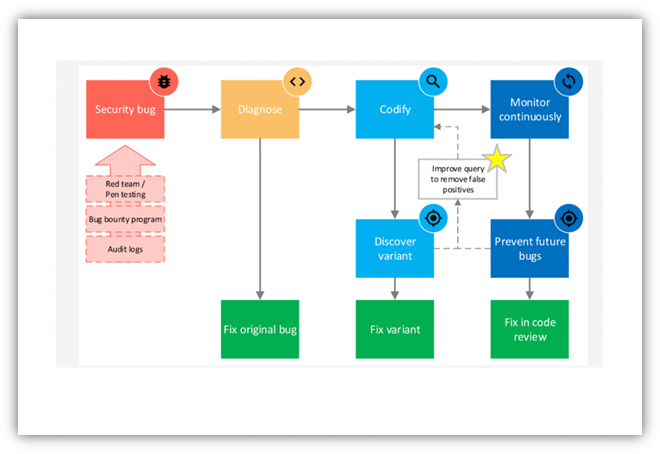
Kubernetes and Container Security
Containerization and Kubernetes orchestration accelerate delivery but also introduce unique security challenges. Proper image scanning, network segmentation, and role-based access control (RBAC) are non-negotiable.

Real-World Example: Kubernetes and Container Security
Scenario (Problem):
DataLogix, a data analytics startup, uses Azure Kubernetes Service (AKS) for microservices. They notice container sprawl—too many images from different sources. Additionally, a developer accidentally left a privileged container running, giving it host access. One malicious script exploited a known vulnerability to pivot laterally.
Solution:
They standardized on a minimal base image, enforced container scanning with tools like Twistlock or Aqua, and restricted container privileges. Network policies now segment microservices by namespace, and secrets are stored in Azure Key Vault with strict RBAC settings.
Best Practices:
- Use container scanning at every build.
- Apply RBAC to the Kubernetes cluster, granting minimal permissions.
- Implement network policies to limit lateral movement between pods.
Action Steps:
- Consolidate Container Images: Decide on a single, hardened base image.
- Enforce Scanning: Integrate scanning tools into your pipeline.
- Implement RBAC: Restrict cluster access by role (developer, admin, ops).
- Secure Secrets: Store secrets in Azure Key Vault or sealed secrets, never in code.
Worksheet: Securing Kubernetes and Containers
- List container images to secure (e.g., app containers, monitoring containers).
- Specify scanning tools for images and registries (e.g., Aqua, Twistlock).
- Define RBAC roles for Kubernetes cluster access.
- Write example network policies for pod communication.
- Plan out secrets management strategy using Azure Key Vault.
Questionnaire: Kubernetes Security Assessment
- Have all container images been scanned for vulnerabilities?
- Are pod-level security policies enforced in Kubernetes?
- How are you managing secrets securely in AKS?
- Do you have controls in place for lateral movement within the cluster?
- What is your remediation process for flagged vulnerabilities?
Monitoring and Response
Visibility across the entire pipeline and production environment is crucial for detecting anomalies, auditing events, and responding to incidents quickly.
Real-World Example: Monitoring and Response
Scenario (Problem):
ZetaLogistics runs dozens of microservices on AKS. They lack centralized logging—when something breaks, the DevOps team scrambles to SSH into multiple pods. They also find out about production outages from customer complaints rather than real-time alerts.
Solution:
They set up Azure Monitor and log analytics, consolidating logs from pipelines, cluster events, and container output. A well-structured dashboard displays CPU usage, memory usage, and pipeline success rates. Azure Sentinel sends alerts to Slack when thresholds are exceeded. An incident response playbook details who to call, how to escalate, and how to roll back quickly if needed.
Best Practices:
- Collect logs from all critical systems (pipelines, containers, security tools).
- Set clear thresholds for alerts; too many false alarms breed complacency.
- Train your team on how to respond to incidents, including communication protocols and root-cause analysis.
Action Steps:
- Centralize Logs: Use Azure Monitor or third-party SIEM tools to collect logs in one place.
- Define Dashboards: Show real-time pipeline status, cluster health, and security alerts.
- Create Alert Rules: Notify the right team members for each severity level.
- Run Incident Drills: Test your incident response plan at least quarterly to ensure readiness.
Worksheet: Monitoring and Incident Response
- What metrics will you monitor (e.g., pipeline success rate, security alerts)?
- Create a monitoring dashboard structure (include log sources).
- Develop alert rules (e.g., for failed builds, policy violations).
- Specify tools to integrate (e.g., Azure Monitor, Sentinel).
- Plan routine audit schedules for DevSecOps processes.
Questionnaire: Strengthening Monitoring Practices
- Are log files being collected from all critical systems?
- How frequently do you review security alerts and audit logs?
- Have you tested your alert thresholds for false alarms?
- How do you ensure visibility into multi-cloud environments?
- Are you regularly updating your monitoring and response workflows?
Conclusion
Adopting a DevSecOps culture in Azure is a strategic investment that pays dividends in security, compliance, and operational efficiency. By systematically addressing:
- Project Setup (clear governance and structure),
- CI/CD Pipelines (automated, repeatable, and secure),
- Security Integration (continuous scanning and policy enforcement),
- Kubernetes & Container Security (robust orchestration with minimal risk),
- Monitoring & Response (real-time visibility and rapid incident resolution),
Next Steps
- Review the worksheets and questionnaires in each chapter to identify immediate gaps.
- Assemble a cross-functional team (Dev, Ops, Sec, QA) to outline a DevSecOps roadmap.
- Establish metrics for success (e.g., vulnerability count over time, pipeline stability, release velocity).
- Iterate and refine—DevSecOps is not a one-time project, but a continual journey of improvements.
Relevant Links
- Microsoft Azure DevOps Documentation – Comprehensive guide to Azure DevOps services, including pipelines, repositories, and artifacts.
- Azure Key Vault Documentation – Learn how to securely manage secrets, keys, and certificates for your applications.
- Azure Pipelines Documentation – Step-by-step guidance for building and deploying CI/CD pipelines.
- OWASP DevSecOps Guidelines – Industry-standard best practices for integrating security into software development.
- CNCF DevSecOps Landscape – Explore tools and services for secure cloud-native development.
- NIST Cybersecurity Framework – A widely recognized framework for integrating security into development lifecycles.
- Azure DevSecOps Best Practices Blog – Insights and updates from Microsoft Azure’s official blog.
- HashiCorp Terraform and Azure Integration – Use Terraform for secure infrastructure as code (IaC) in Azure.
- Stack Overflow: Azure DevSecOps – Community Q&A for resolving DevSecOps challenges in Azure.
- Azure GitHub Repositories – Access open-source projects and resources from the Azure team.
Try Hostinger’s Cloud Professional or Cloud Enterprise plans today and take your online presence to the next level.
Looking to keep your browsing secure? I recommend PIA VPN for top-notch encryption and privacy protection.
Get it here and secure your online activity today.
u




Leave a Reply
Want to join the discussion?Feel free to contribute!