Microsoft Entra Verified ID Made Simple: Options and Onboarding Best Practices
Microsoft Entra Verified ID offers organizations a secure, scalable, and compliant solution for managing digital identities. By using this technology, organizations can verify identities across users, devices, and applications, while adhering to stringent compliance requirements and implementing best practices for Azure security.
What Is Microsoft ENTRA Verified ID?
Microsoft ENTRA Verified ID is a decentralized identity solution that allows organizations to verify and manage digital identities securely. This technology leverages industry standards like decentralized identifiers (DIDs) and verifiable credentials to create trusted interactions between issuers, holders, and verifiers.
Why Choose Verified ID?
- Enhanced Security: Drops reliance on passwords, reducing the risk of credential theft and phishing attacks.
- Compliance-Ready: Meets GDPR, HIPAA, and other regulatory requirements for identity management.
- Interoperability: Works across Microsoft Azure and other ecosystems, providing flexibility for diverse organizational needs.
Key Features and Benefits
| Feature | Benefit |
| Decentralized Identity | Users control their credentials, enhancing privacy and reducing central risks. |
| Verifiable Credentials | Issue tamper-proof credentials to ensure trust across interactions. |
| Seamless Integration | Integrates with Azure Active Directory (AAD) and other Microsoft services. |
| Scalability | Supports large-scale deployments for enterprises and governments. |
| Automation | Streamlines credential issuance and verification processes. |
| Built-In Compliance Tools | Aligns with major global standards and frameworks for identity management. |
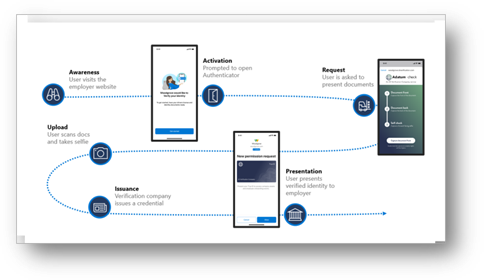
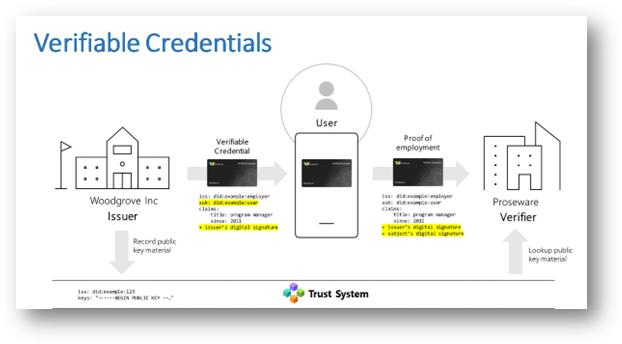
Use Cases for Verified ID
Enterprise Use Cases
- Employee Onboarding
- Description: Issue digital credentials to new employees for secure access to enterprise applications.
- Business/Security Results: Reduced onboarding time by 50%, enhanced access security, and minimized human error.
- Access Management
- Description: Enable seamless and secure access to internal systems through verified credentials.
- Business/Security Results: Improved operational efficiency and reduction in unauthorized access incidents by 30%.
Educational Institutions
- Student Identity Verification
- Description: Provide students with verifiable digital IDs for campus services, exams, and external verifications.
- Business/Security Results: Simplified administrative workflows and reduced risk of identity fraud.
Government and Public Sector
- Citizen Services
- Description: Issue verifiable IDs for citizens to access services like healthcare, taxation, and voting.
- Business/Security Results: Enhanced trust in government services and streamlined service delivery.
Healthcare Organizations
- Patient Identity Management
- Description: Ensure secure access to medical records and compliance with HIPAA.
- Business/Security Results: Improved patient experience and minimized HIPAA violations.
Onboarding Verified ID in Your Organization
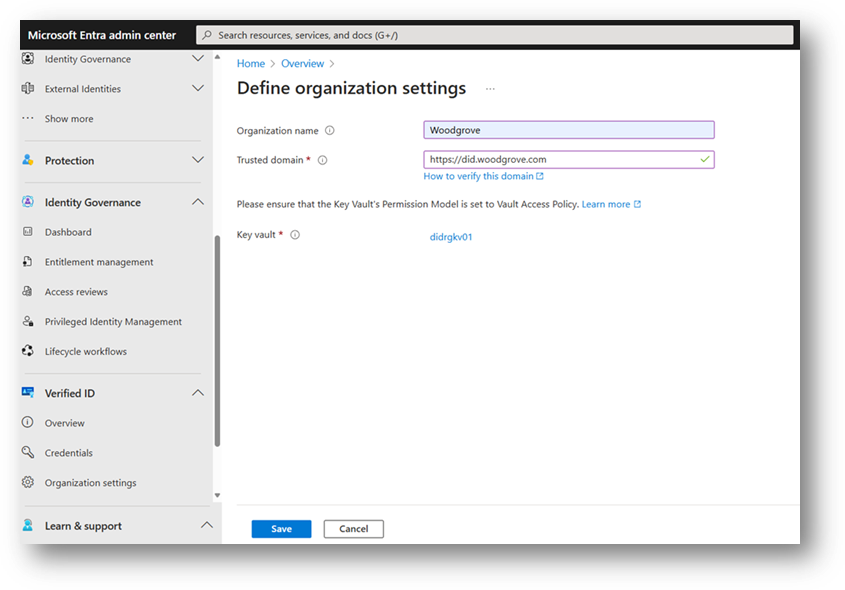
Step 1: Assess Organizational Needs
- Find key areas where Verified ID can improve identity management.
- Engage stakeholders to understand user and system requirements.
Step 2: Plan Your Deployment
- Define the scope of the first implementation (e.g., department, region, or service).
- Align goals with compliance and security requirements.
Step 3: Integrate with Existing Systems
- Connect Verified ID with Azure Active Directory and other identity platforms.
- Leverage Microsoft’s APIs for custom application integration.
Step 4: Configure Credential Issuance
- Use Microsoft Entra Verified ID templates to issue verifiable credentials.
- Test the issuance process with a pilot group.
Step 5: Implement User Training and Documentation
- Educate users on how to use and manage their digital credentials securely.
- Provide clear documentation for administrators and end-users.
Step 6: Monitor and Optimize
- Use Azure Monitor and Microsoft Sentinel to track adoption and detect issues.
- Continuously refine processes based on feedback and analytics.
Compliance and Security Best Practices
- Role-Based Access Control (RBAC)
- Ensure only authorized personnel can issue or verify credentials.
- Private Endpoints and Network Security
- Use private endpoints for secure communication between resources.
- Enforce NSGs to restrict unauthorized access.
- Data Encryption
- Encrypt all data at rest using Azure Key Vault.
- Enforce TLS for data in transit.
- Auditing and Logging
- Enable logging for credential issuance and verification processes.
- Regularly review logs for anomalies.
- Policy Enforcement with Azure Policy
- Create policies to ensure adherence to compliance frameworks.
- Regular Security Assessments
- Conduct periodic reviews to identify vulnerabilities and gaps.
Monitoring and Incident Response
Monitoring Tools
- Azure Monitor/Log Analytics
- Track the performance and availability of Verified ID services.
- Microsoft Sentinel
- Detect and respond to threats using built-in incident response playbooks.
Incident Response Plan
- Define roles and responsibilities for handling breaches or system failures.
- Conduct regular drills to ensure readiness.
- Use automation to isolate affected systems and mitigate risks.
Worksheets and Questionnaires
Worksheet: Deployment Planning
- What systems will Verified ID integrate with?
- Who are the stakeholders for the implementation?
- What are the compliance requirements for your region or industry?
- How will credentials be issued, revoked, and checked?
- What training will be needed for end-users and administrators?
- What metrics will define success for this deployment?
- What resources (technical and human) are needed for the project?
- What is the timeline for rollout?
- How will feedback be collected, documented, and acted upon?
- Are backup systems in place for credential recovery?
Questionnaire: Security and Compliance Readiness
- Are all endpoints configured with TLS for secure data transmission?
- Is encryption enabled for all stored data?
- Are role-based permissions configured appropriately?
- Are there automated alerts for unauthorized access attempts?
- Is there a documented policy for credential lifecycle management?
- Are private endpoints in use for critical Verified ID services?
- Is a backup and recovery plan in place for credential data?
- Are administrators trained on compliance requirements?
- Are logs reviewed regularly for suspicious activities?
- Is an incident response plan documented and tested?
Conclusion
Microsoft ENTRA Verified ID empowers organizations to streamline identity verification while enhancing security and compliance. By following the outlined onboarding process and adopting best practices, organizations can unlock the full potential of this technology to build a robust identity management system.
Boost Your Website Performance with Hostinger’s Cloud Hosting!
Looking to keep your browsing secure? I recommend PIA VPN for top-notch encryption and privacy protection.
Get it here and secure your online activity today.
© 2025 MHartson Consulting. All rights reserved.




Leave a Reply
Want to join the discussion?Feel free to contribute!